Understanding and Defending Against Supply Chain Cyber Attacks
In the intricate web of modern business operations, the security of supply chains has ascended to a critical concern. As organizations increasingly depend on a global network of suppliers for materials, products, and services, the pathways for cyber attackers to infiltrate have expanded. Supply chain cyber attacks exploit these networks,
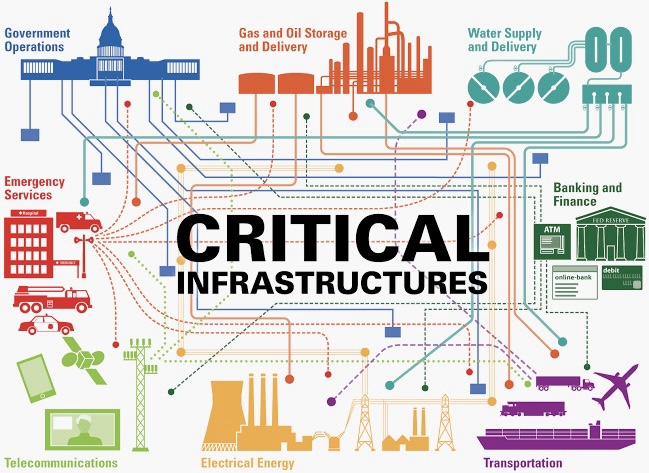
Read moreSecuring Critical Infrastructure: Cyber Threats and Resilience Strategies
In an era where digital interconnectedness defines our critical infrastructure, the imperative to secure these vital systems against evolving cyber threats has never been more crucial. This comprehensive guide aims to unravel the intricacies of safeguarding critical infrastructure, addressing the dynamic landscape of cyber threats and presenting resilience strategies to
Read moreHealthcare Cybersecurity: Protecting Sensitive Patient Data in the Digital Era
In the rapidly evolving landscape of healthcare, the digitization of patient records and medical processes has revolutionized the industry. However, this digital transformation brings with it a pressing concern: the need to protect sensitive patient data from the ever-growing threat of cyberattacks. This article explores the challenges healthcare organizations face
Read morePrivacy and Security in the Age of Smart Homes: A Comprehensive Guide
Welcome to the era of smart homes, where convenience meets connectivity. As we embrace the myriad benefits of interconnected devices, it becomes paramount to prioritize security and protect our privacy. In this comprehensive guide, we will delve into actionable steps to fortify your smart home against potential threats, ensuring a
Read moreSocial Engineering Attacks: How to Recognize and Defend Against Them
In an era where digital threats continue to evolve, understanding and defending against social engineering attacks have become critical for individuals and organizations alike. This comprehensive guide aims to provide an in-depth exploration of common techniques, red flags, and proactive defense strategies, offering practical insights to enhance your cybersecurity posture.
Read moreBiometric Authentication: The Future of Secure Access Control
Secure access management is vital in a society that is becoming more digital and networked. Biometric authentication has become a viable alternative as conventional authentication techniques like PINs and passwords have shown to be insecure and inconvenient. Biometrics uses distinctive behavioral and physical characteristics to confirm an individual's identity. This
Read moreAl-Powered Threat Detection: Enhancing Cybersecurity with Machine Learning
Organizations are facing a difficult battle in protecting their digital assets in an era characterised by more sophisticated cyber threats. Even if they can be somewhat effective, traditional cybersecurity procedures frequently find it difficult to keep up with the changing threat landscape. Step into the world of artificial intelligence (AI)
Read moreRansomware Resilience: Strategies to Protect Your Business in the Digital Age
In today's digital age, ransomware attacks have emerged as a relentless and evolving threat to businesses of all sizes. These malicious attacks can disrupt operations, compromise sensitive data, and inflict significant financial damage. To safeguard your business in this digital landscape, it's crucial to adopt robust strategies for ransomware resilience.
Read moreSecuring AI and ML Systems from Ethical Hacks: Safeguarding Cybersecurity’s Gatekeepers
In the realm of cybersecurity, Artificial Intelligence (AI) and Machine Learning (ML) have emerged as powerful gatekeepers, fortifying digital defenses against evolving threats. However, as these technologies play a pivotal role in safeguarding our digital world, the need to protect them from potential ethical hacks and adversarial manipulations becomes paramount.
Read moreAI-Generated Deepfakes and Cybersecurity Threats
Artificial Intelligence (AI) and deep learning technologies have unlocked innovative possibilities, but they also come with potential risks. One of the emerging challenges in the realm of cybersecurity is the growing threat of AI-generated deepfakes. In this blog post, we delve into the rising concern of AI-generated deepfakes in cyber
Read more