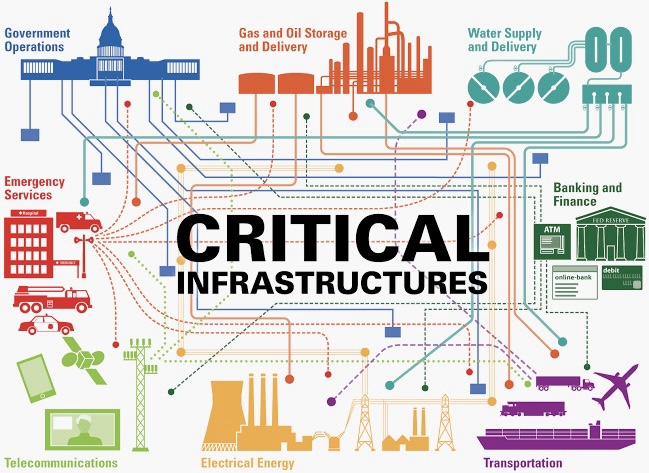
Securing Critical Infrastructure: Cyber Threats and Resilience Strategies
In an era where digital interconnectedness defines our critical infrastructure, the imperative to secure these vital systems against evolving cyber threats has never been more crucial. This comprehensive guide aims to unravel the intricacies of safeguarding critical infrastructure, addressing the dynamic landscape of cyber threats and presenting resilience strategies to
Read moreBlockchain and Cybersecurity: Exploring the Link Between the Two
In the ever-evolving landscape of cybersecurity, blockchain technology has emerged as a transformative force. This comprehensive exploration aims to unravel the intricate relationship between blockchain and cybersecurity, delving into how this decentralized ledger technology can significantly bolster defenses against the relentless tide of cyber threats. Blockchain Basics:At its core, blockchain
Read moreHealthcare Cybersecurity: Protecting Sensitive Patient Data in the Digital Era
In the rapidly evolving landscape of healthcare, the digitization of patient records and medical processes has revolutionized the industry. However, this digital transformation brings with it a pressing concern: the need to protect sensitive patient data from the ever-growing threat of cyberattacks. This article explores the challenges healthcare organizations face
Read morePrivacy and Security in the Age of Smart Homes: A Comprehensive Guide
Welcome to the era of smart homes, where convenience meets connectivity. As we embrace the myriad benefits of interconnected devices, it becomes paramount to prioritize security and protect our privacy. In this comprehensive guide, we will delve into actionable steps to fortify your smart home against potential threats, ensuring a
Read moreSocial Engineering Attacks: How to Recognize and Defend Against Them
In an era where digital threats continue to evolve, understanding and defending against social engineering attacks have become critical for individuals and organizations alike. This comprehensive guide aims to provide an in-depth exploration of common techniques, red flags, and proactive defense strategies, offering practical insights to enhance your cybersecurity posture.
Read moreSecuring Cloud Data: Best Practices for Data Protection in the Cloud
Cloud computing has fundamentally altered how businesses handle, store, and use data in today's digitally driven world. The flexibility and scalability of cloud services have many advantages, but there are certain security risks as well. Data protection in the cloud is crucial for both consumers and enterprises, as concerns over
Read moreThe Dark Web Unveiled: Understanding the Hidden Online World
Connecting billions of people globally, the internet is a vast and diverse medium that creates new opportunities for trade, dialogue, and information exchange. All of us are, however, aware of the mysterious, murky area of the internet known as "the dark web." Both tech aficionados and law enforcement agencies have
Read moreCryptocurrency Security: How to Safeguard Your Digital Assets
It is crucial to protect your digital assets as cryptocurrencies continue to gain traction in the financial and investment industries. Since cryptocurrencies are fully digital, unlike conventional banking systems, they present special security issues. Maintaining your peace of mind as well as your financial worth are two reasons to make
Read moreCybersecurity for Small Businesses: Essential Tips to Stay Protected
Cyberattacks are a major threat to small businesses in today's increasingly digital world. Cybercriminals are aware that many small firms lack the strong security protocols of larger companies, leaving them open to financial losses, reputational harm, and data breaches. It's crucial to comprehend and put into practice thorough cybersecurity procedures
Read moreBiometric Authentication: The Future of Secure Access Control
Secure access management is vital in a society that is becoming more digital and networked. Biometric authentication has become a viable alternative as conventional authentication techniques like PINs and passwords have shown to be insecure and inconvenient. Biometrics uses distinctive behavioral and physical characteristics to confirm an individual's identity. This
Read more